Security at Tellen
At Tellen, our top priority is safeguarding clients’ data. How do we achieve this? By keeping things simple: We stay out of our clients’ data entirely. Every bit of information resides within their own cloud environment. And it doesn’t stop there—we embed our entire infrastructure and software right into their environment as well.
This approach ensures that all AI models, databases, file storage, and more remain under their control. Their data—encrypted both at rest and in transit—never strays from their network, securely flowing through Microsoft’s backbone or encrypted tunnels directly to their users’ machines.
We operate on the principles of zero trust and least privileged access. What does this mean? Even within their own environment, access is tightly controlled. Permissions are granted only on a need-to-know basis, and every request for access is rigorously scrutinized, logged, and regularly audited to maintain ironclad security.
And it's not just about infrastructure and networking. Our software is designed with security woven into every line of code. From the very start, we employ automated end-to-end testing, unit and mutation testing, along with vulnerability scanning at every development stage.
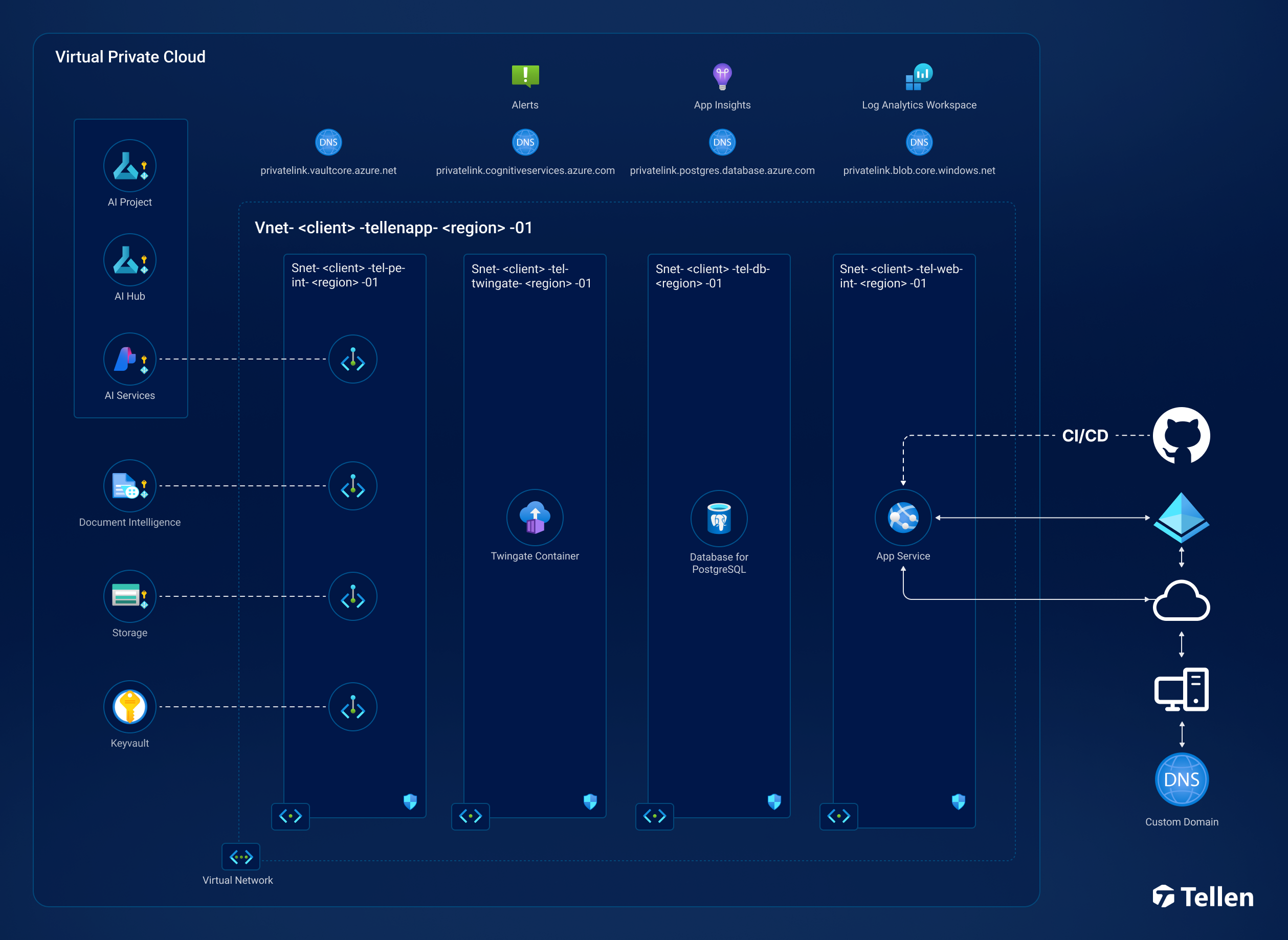
Network Security

66d772fb0e97cfc759b22398_66d77101d7b89283e852b6a4_image%20(1).png
Take a look at our network diagram, and you'll see that all endpoints—whether for AI models, databases, or storage containers—are dedicated exclusively to our clients. Data moves solely through the Microsoft backbone, avoiding the public internet entirely. The virtual network is meticulously segmented into subnets, with strict controls over which ports are accessible between them. The only element visible to the outside world is the web app, which, if our clients prefer, can be accessed through Twingate—a modern, zero trust, peer-to-peer connection that far surpasses traditional VPN technology. We can even restrict access down to specific IP addresses.
Model Training and Inference: Privacy Assured At Tellen, your prompts, completions, embeddings, and training data are treated with the highest level of confidentiality. They are:
- NOT available to other customers: Your data remains your own. It is never shared with or exposed to other customers.
- NOT available to OpenAI: OpenAI does not have access to your data at all.
- NOT used to improve OpenAI models: Your data does not contribute to refining OpenAI’s models.
- NOT used to improve Tellen, Microsoft, or other products or services: Your data is exclusively for your use.
- NOT used for automatically improving any AI models: The models we use are entirely stateless unless you explicitly choose to fine-tune them with your training data, in which case those fine-tuned models will remain exclusive to your use, ensuring that your proprietary insights remain within your control.
For more on the relationship between Microsoft and OpenAI, see this article.
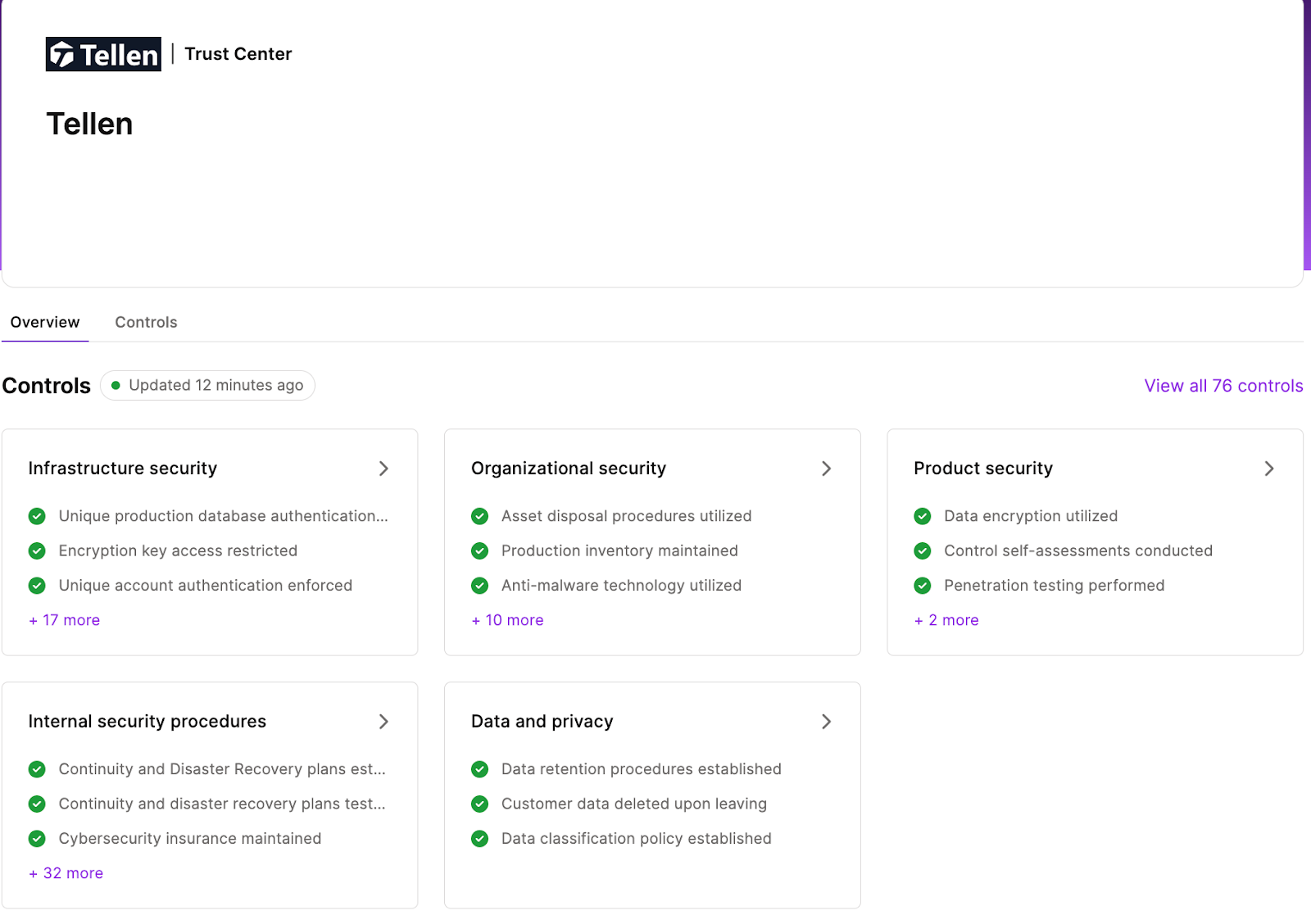
Compliance We’re undergoing our SOC-2 audit, but we’re not waiting around for that to assure you of our compliance. Independent verifications by Vanta already confirm our adherence to all SOC-2 security and privacy standards. For live, independent confirmation, you can visit trust.tellen.ai at any time.
66d77119b9e708220c272563_AD_4nXehTwfk-6-HlhKfwcqWst5QDbD-SkKoo6hGH1_Di2pHo0ogLSFyMVDJdIyJuymoatjfNu-DLIkov5AEwPlkjUwfr3k0br-LSQDNwMZZn29z0N217XkXM0YGWb0M2UDPjU7B2LZeoLBdVTuNXQn-9NK-rpJB.png
Encryption All data, whether at rest or in transit, is protected by industry-leading encryption protocols. We employ AES-256 encryption for data storage and TLS 1.3 for data transmission, ensuring that sensitive information remains secure from unauthorized access.
Access Control Access to critical systems and data is tightly controlled at Tellen. We enforce multi-factor authentication (MFA) across all access points, implement role-based access controls (RBAC), and conduct regular compliance audits to maintain our high security standards. Only a select group of client-vetted US-based employees have access to client data, while the majority of our engineers work in separate development environments focused on tasks like coding and database management without ever touching client data. Tellen’s access can be unilaterally removed by clients at any time.
Incident Response Tellen is prepared for any security threat with a comprehensive incident response plan. We continuously monitor for potential threats, and if an incident occurs, affected systems are immediately isolated. Our predefined investigation and resolution process kicks in, ensuring swift and effective action. Our incident response team is on standby 24/7, ready to address any security concerns at a moment’s notice.
Employee Training We know that the strongest security measures can be undermined by human error. That’s why every Tellen employee undergoes regular security training to stay sharp on the latest threats and best practices. Our training covers everything from phishing awareness to secure coding practices and data protection regulations, ensuring that our team is always prepared to uphold the highest standards of security.
A Commitment to Security At Tellen, security is not just a checkbox—it's a fundamental part of everything we do. By placing our infrastructure and software entirely within our clients' cloud environments, adhering to strict security principles, and continually evolving our practices, we ensure that our clients' data is always protected. Our commitment to security is unwavering because we understand that in today’s digital world, trust is everything. When you choose Tellen, you’re not just choosing a service provider—you’re choosing a partner dedicated to safeguarding your business and its most valuable assets.